AWS Site-to-Site VPN: Securely Connecting Your On-Premises Network to AWS
Please use the menu below to navigate the article sections:

Amazon Web Services (AWS) is a well-known cloud service company that offers a wide range of solutions to businesses of all sizes. The secure connection of local networks to cloud infrastructure is a critical component of cloud adoption. AWS Site-to-Site VPN enables clients to connect from their on-premises network to the AWS side network and set routing to route traffic to the target network. Site-to-site VPNs are the preferred choice for numerous organizations with multiple offices in various geographic areas. These VPNs facilitate continuous access and utilization of the corporate network across different locations.
Benefits of using AWS Site-to-Site VPN
- AWS Site-to-Site VPN encrypts all data transported between your on-premises network and AWS. This encryption creates a safe path for sensitive data, preventing unauthorized access or interception.
- It enables organizations to effortlessly link their on-premises network to the AWS cloud. This allows on-premises network resources to safely connect with AWS services, resulting in a hybrid architecture arrangement.
- Amazon CloudWatch Logs allows you to monitor, store, and access log files for your AWS Client VPN connection logs. Relevant log data is available from CloudWatch Logs.
- AWS Site-to-Site VPN eliminates the requirement for leased lines or hardware-based VPN gear. This reduces the expenses of maintaining and administering traditional networking infrastructure.
Importance of securely connecting on-premises network to AWS
- Many companies store and analyze sensitive data in on-premises networks. By establishing a secure connection to AWS, you can securely transfer data to and from the cloud.
- Certain industries and regulatory regimes impose severe security and compliance requirements. By securely connecting on-premises networks to AWS, organizations can meet these standards while protecting privacy and integrity.
- Organizations frequently use a hybrid architecture that combines on-premises infrastructure with cloud resources. Secure communication allows for seamless integration of the two environments, allowing for more efficient operations and data transmission.
Setting up AWS Site-to-Site VPN
Prerequisites for setting up Site-to-Site VPN
- You should have two VPCs, each with one subnet. To avoid routing conflicts, the CIDR block of the VPC should not coincide with that of your on-premises network.
- On your side of the VPN connection, you need to have a customer gateway device or software application, and you will need to know the manufacturer, platform, software version, IP address, routing type, and BGP ASN (if relevant).
- You must have a target gateway in AWS (virtual private gateway or transit gateway) and its ASN as an independent network under the control of a single scope of administration.
- You need to connect the target gateway with your VPC.
- A VPC-attached Internet Gateway is necessary to link the VPC to the Internet and eventually to your on-premises network.
- To ensure traffic is directed effectively via the VPN connection, you must properly establish the route tables for your subnets within the VPC.
- To enable incoming and outgoing traffic for your VPN connection, you need to update your security group.
Steps for configuring Site-to-Site VPN
Creating a Virtual Private Gateway
Using “AWS Management Console“, navigate to the VPC Service and click on “Virtual Private Gateway” in the sidebar menu under the “Virtual Private Network” category.
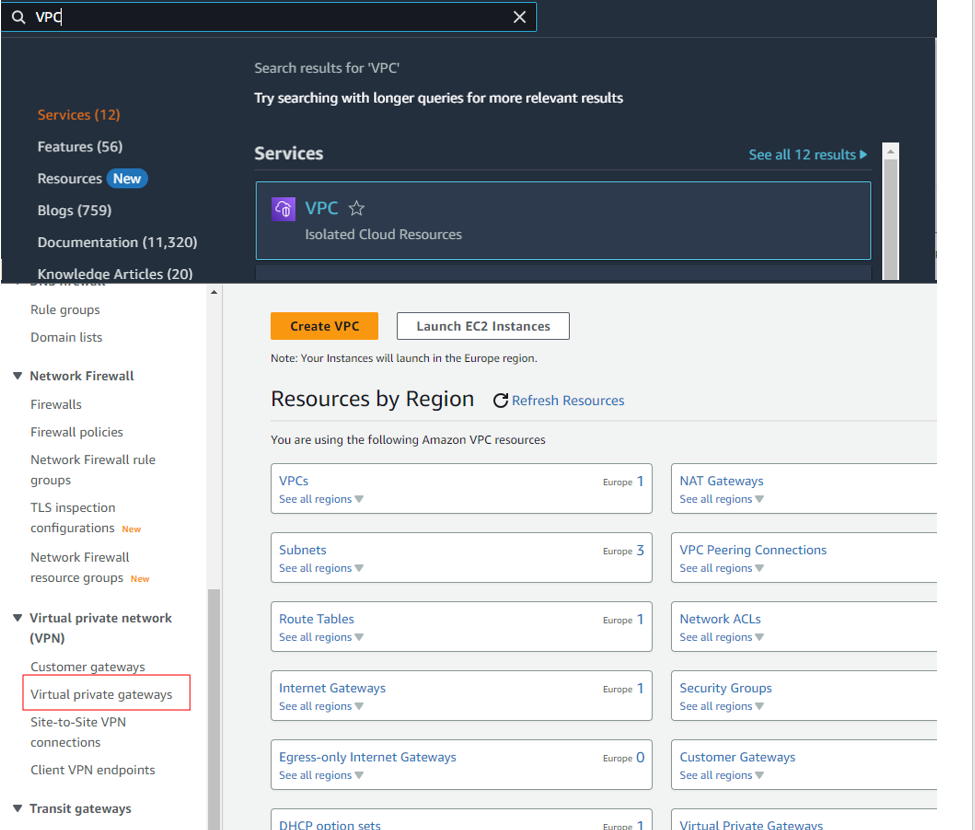
Once you navigate to the “Virtual Private Gateway” dashboard, click on the “create new virtual private gateway” button and enter the name of VPG in the prompt.
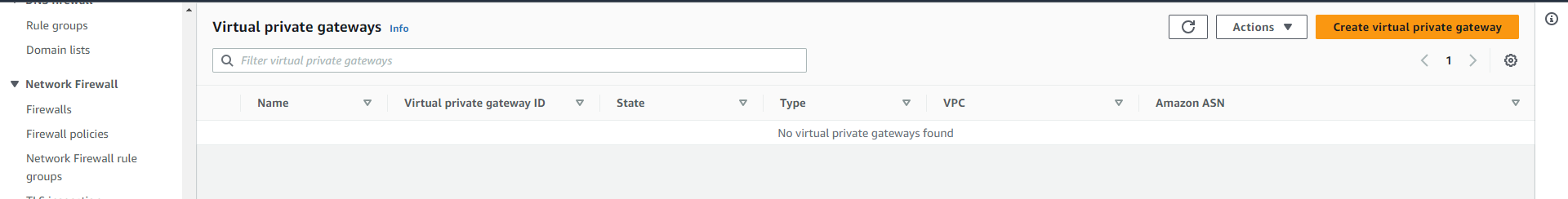
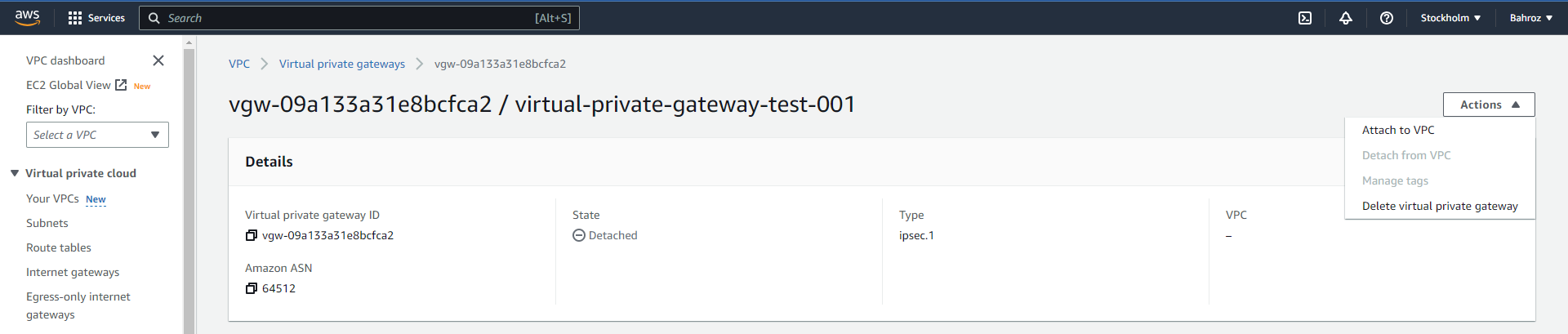
Once the VPG is created, select that VPG and attach it with the VPC with which you want to create the VPN connection by clicking on “Action”.
Creating a Customer Gateway
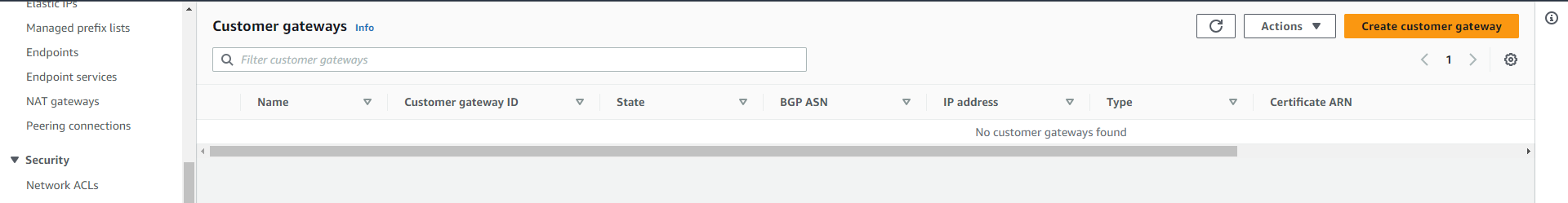
From the VPC service dashboard, you need to click on “Customer Gateways” in the Sidebar menu under the “Virtual Private Network” Category.
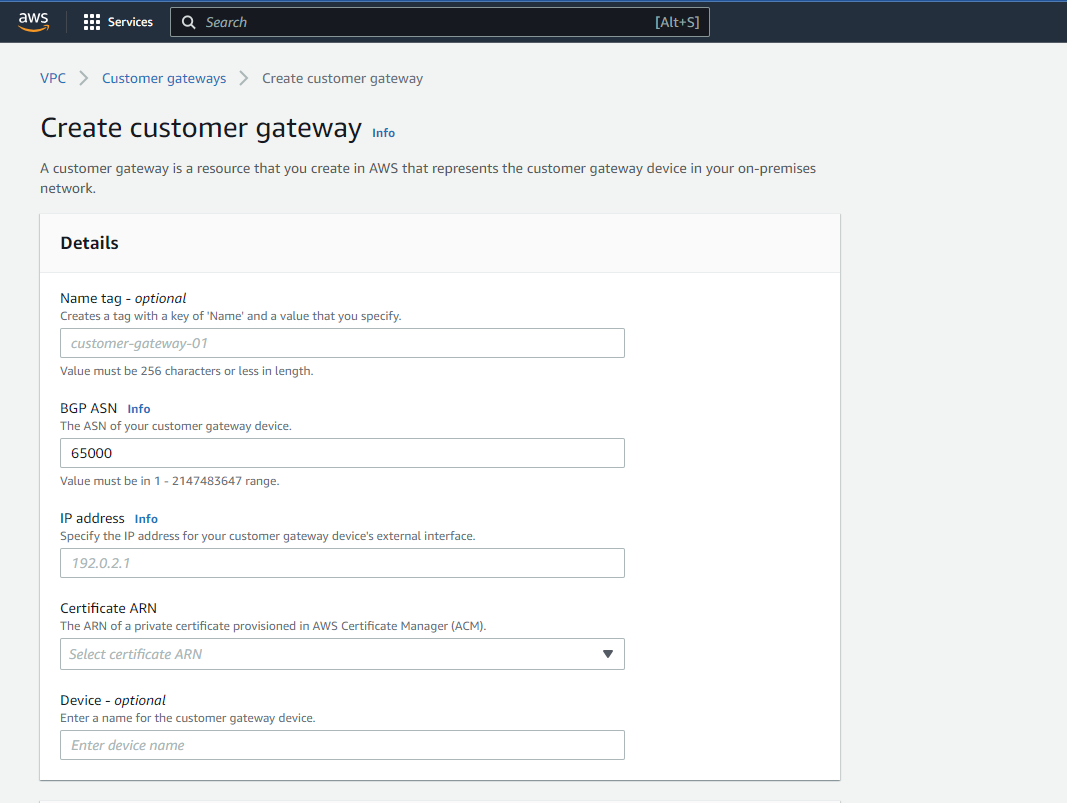
Once you navigate to the “Customer Gateways” dashboard, click on the “Create new customer gateway” button and enter the information (IP address, BGP ASN etc.) related to the customer gateway in the next prompt. As previously mentioned, you need to have all information related to the customer gateway device.
Creating a Site-to-Site VPN Connection
From the VPC service dashboard, you need to click on “Site-to-Site VPN Connections” in the sidebar menu under the “Virtual Private Network” category.
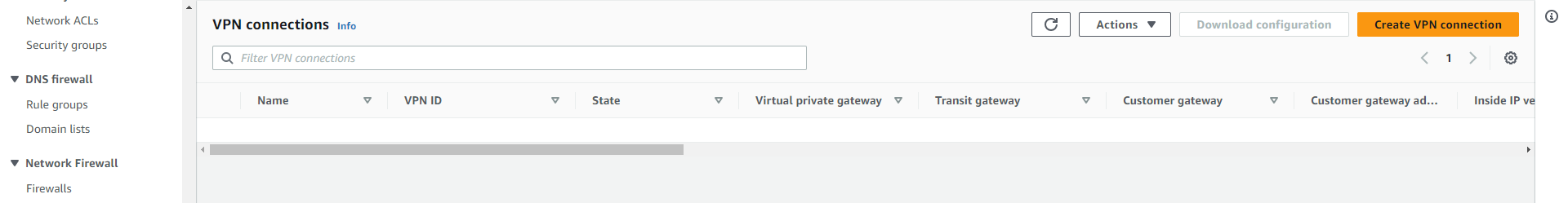
Once you navigate to the “Site-to-Site VPN Connections” dashboard, click on the “Create new VPN Connection” button, and in the prompt, just enter the information that includes the VPN connection name, and then select Virtual Private Gateway and Customer gateway in the dropdowns. You can now also configure the routing options.
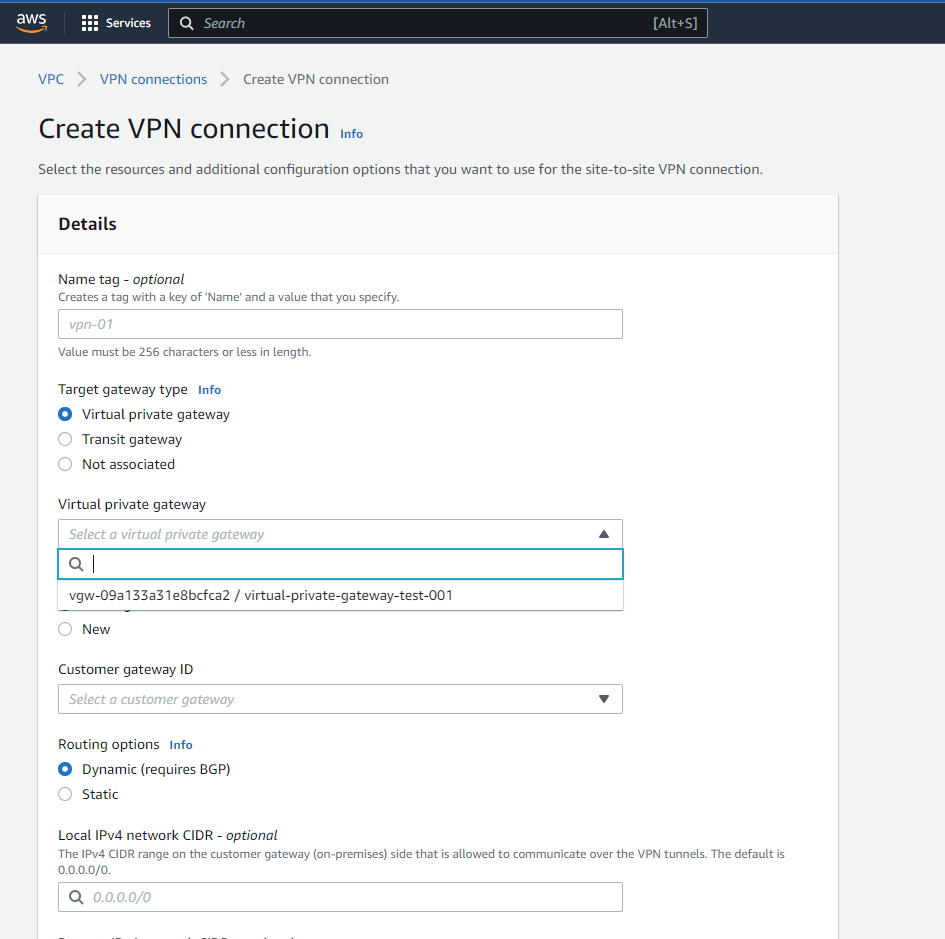
Updating your Routing Tables
Click on “Route Tables” in the sidebar menu under the “Virtual Private Cloud” category from the VPC service dashboard.
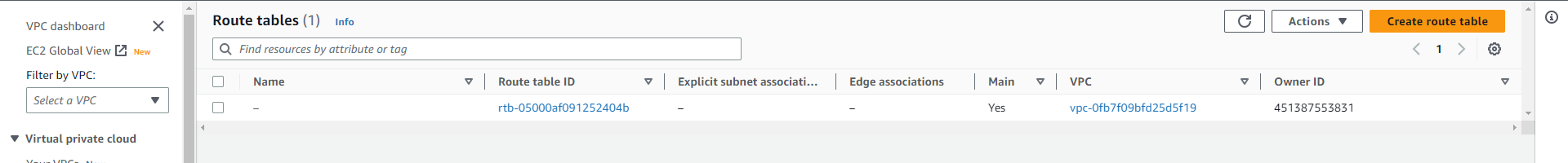
You must click on the specific route table that appears in the “Route Table” panel for you to edit your path table connected to VPC.
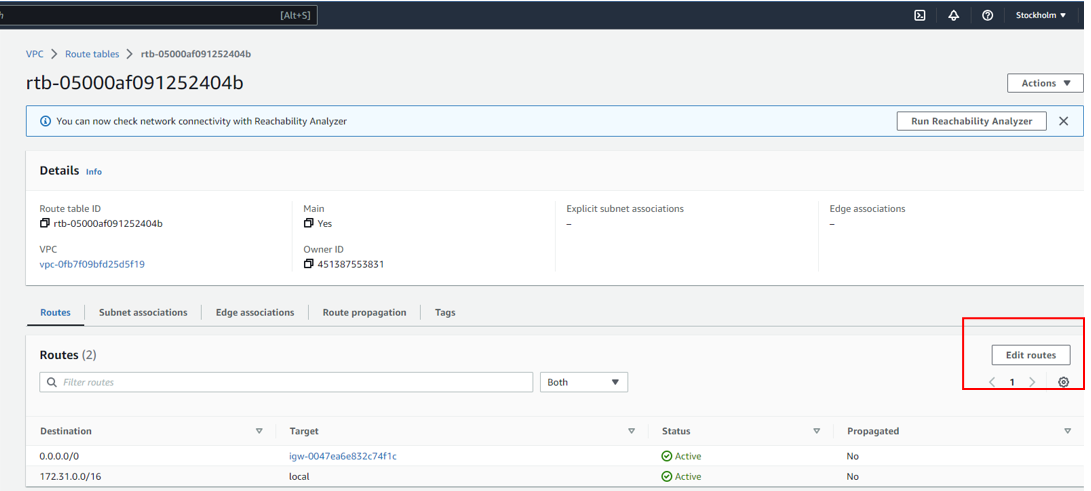
You need to add a route to the destination CIDR block on your network to direct traffic to your VPN connection. For that purpose, when you navigate to the specific route table, click on the “Edit Routes” button in the “Routes” section, and in the next prompt, you need to add a route to the destination CIDR block on your network.
Best practices for configuring Site-to-Site VPN
- Use strong encryption algorithms and safety protocols to protect your VPN traffic.
- Enable monitoring and logging of VPN connections to keep an eye on their performance and detect any possible problems.
- To ensure that redundancy is implemented, you need to set up several VPN connections over different accessibility zones or regions.
- You need to regularly review and update the settings for your VPN connections, routing tables or security groups to keep up with ever more demanding network requirements and safety best practices.
Security considerations
Encryption and Authentication Options for Site-to-Site VPN
IPSec VPN: IPSec is among the most commonly used security protocols for site-to-site (Virtual Private Networks). A high level of encryption and authentication is provided to you. In addition, encryption protocols such as AES 256, SHA256 and RSA are supported.
SSL VPN: Allowing connections to be made via web browsers gives you flexibility and security for your site-to-site VPNs. SSL VPN additionally supports strong encryption and authentication.
Certificate-based authentication: Organizations may utilize digital certificates to enable more secure authentication. A certificate authority (CA) manages certificates using a public key infrastructure (PKI).
Configuring Security Groups and Network Access Control Lists (NACLs)
Security Groups:
Security groups act as a virtual firewall for your Amazon Web Services instances, allowing you to control inbound and outbound traffic. Changes to security group rules can be modified at any time. All instances associated with a security group will automatically get the updated rules.
Network Access Control Lists (NACLs):
NACLs serve as a rule-based tool that allows you to restrict network traffic in and out of one or more subnets within your Virtual Private Cloud (VPC). NACLs function at the subnet level, whereas Security Groups operate at the instance level.
Monitoring and logging options for Site-to-Site VPN
CloudWatch: For your AWS resources, CloudWatch is a service that collects and tracks metrics, alarms, and logs. With CloudWatch, you can check the state and data in and out of your VPN tunnels.
CloudTrail: The CloudTrail API call monitoring service allows you to monitor API calls associated with your site-to-site VPN connections, such as the creation, modification, deletion or removal of customer gateway and virtual private gateways.
Advanced topics
High availability options for Site-to-Site VPN
Create multiple VPN connections from your client gateway device to different virtual private gateways or transit gateways to improve the availability and stability of your Site-to-Site VPN connection. Dynamic routing protocols such as BGP can also be used to automatically fail over to the best available path.
Connecting multiple on-premises networks to AWS
Multiple on-premises networks can be connected to AWS using various ways, such as Site-to-Site VPN, AWS Direct Connect, or AWS Transit Gateway. You can combine these technologies to build hybrid network environments. One approach is that if you are utilizing AWS Transit Gateway, which serves as a hub for connecting multiple on-premises networks to AWS, then Site-to-Site VPN connections can be established from each on-premises network to the Transit Gateway. This enables centralized management and makes connecting on-premises networks to AWS resources easier.
Site-to-Site VPN vs Direct Connect: Which one to choose?
Site-to-Site VPN and Direct Connect are two methods for connecting your on-premises network to your VPCs in a safe and private manner. The public Internet is used as the transport network for Site-to-Site VPN, whereas Direct Connect employs a dedicated network connection from your premises to an AWS location. Several considerations – including performance, cost, scalability, security, and compliance needs – influence the decision between Site-to-Site VPN and Direct Connect.
Use cases for Site-to-Site VPN
Hybrid cloud architectures
Hybrid cloud architecture refers to the combination of two or more different computing environments that can be private cloud on-premise data centers and one or more Public Clouds off-premise Data Centres provided by Third Party Cloud Service Providers such as Azure, Google Cloud etc. By securing the connection between on-premises private cloud infrastructure and a Public Cloud Provider’s data centers, site-to-site VPN is playing an important role in hybrid cloud architecture. This enables data and applications to be transferred seamlessly across different environments, making them seem like they’re part of a single network.
Disaster recovery scenarios
Disaster recovery scenarios entail preparing and implementing solutions to ensure business continuity in the case of natural disasters, system failures, cyberattacks, or other unanticipated occurrences that disrupt usual corporate operations. A Site-to-Site VPN is used to connect the primary data center and disaster recovery site safely and securely. Data replication and synchronization can occur in real time or at regular intervals over this VPN connection, ensuring that the secondary site is always updated with the most recent information. Suppose a disaster strikes and the primary data center becomes unavailable. In that case, the organization can divert traffic and services to the disaster recovery site, minimizing downtime and allowing the business to continue operations.
Remote access VPNs
A VPN (virtual private network) for remote access is intended to offer safe and encrypted remote access to an organization’s internal network resources. A remote access VPN can be configured using several protocols, including IPsec (Internet Protocol Security) and SSL/TLS (Secure Sockets Layer/Transport Layer Security). Once connected, remote users can access internal network resources as if they were physically present in the workplace. This allows you to work remotely, interact with colleagues, and access essential information while keeping your company network secure and intact.
Conclusion
Recap of key points
- The AWS Site-to-Site VPN enables clients to securely connect their on-premises network to the AWS cloud, allowing for encrypted data transmission and hybrid architecture configurations.
- Setting up a virtual private gateway, a customer gateway, a VPN connection, and changing your routing tables are all part of the process.
- Data security is ensured by strong encryption algorithms, security protocols, and robust authentication mechanisms such as IPSec VPN, SSL VPN, and certificate-based authentication.
- Security groups and NACLs manage network traffic, while CloudWatch and CloudTrail provide monitoring and logging capabilities.
- Options for high availability and linking various on-premises networks to AWS enhance flexibility and robustness.
Next steps for setting up AWS Site-to-Site VPN
- The next steps involve constant monitoring, logging, and regular review and updating of your VPN connections, routing tables, and security groups to adjust changing network requirements and adapt security best practices.
- You can also concentrate on developing high-availability solutions, such as generating multiple VPN connections from your client gateway device to separate virtual private gateways or transit gateways.
Future developments in Site-to-Site VPN technology
- While the future of Site-to-Site VPN technology cannot be predicted, we can expect more advancements in security protocols, encryption techniques, and authentication alternatives.
- More user-friendly interfaces and streamlined configuration processes are expected.
- The rise of hybrid and multi-cloud architectures might encourage the development of VPN technologies that will be capable to connect numerous networks across different cloud providers more effectively.
Ready to Take Your Tech Career to the Next Level?
At Digital Cloud Training, we’re dedicated to your success. Our courses offer up-to-date content, equipping you with the expertise to stand out in the competitive tech job market.
Our On-Demand Training allows you to learn at your own pace, fitting seamlessly into your schedule. Dive into the world of cloud computing whenever and wherever suits you best.
Our Challenge Labs provide practical, real-world scenarios where you can apply your newfound knowledge without the risk of unexpected cloud costs. Gain hands-on experience and sharpen your skills.
For those seeking an immersive experience, our Cloud Mastery Bootcamp delivers live, job-ready training. Led by industry experts, this accelerated program can get you certified faster than you thought possible.
It’s time to propel your tech career forward. Join us at Digital Cloud Training and unlock your full potential in the world of cloud computing.





Responses