VPC Interface Endpoint vs Gateway Endpoint in AWS
Please use the menu below to navigate the article sections:
VPC endpoint is a powerful feature of AWS that allows you to establish a private connection between your VPC and other supported AWS services and VPC endpoint services. The VPC endpoints use the PrivateLink feature to make the private connection possible between your VPC and AWS services. Using VPC endpoints, the traffic between your VPC and AWS services does not leave the Amazon network. In other words, VPC endpoints serve as a private connection between your VPC, AWS services, and even your on-premise applications. Using PrivateLink for connectivity means the traffic is not only secure, but latency because of public internet is also reduced.
Using VPC endpoints can be handy in situations like the following:
- If you want to connect your VPC to another AWS VPC but do not have VPN or TGW access
- The other VPC has an overlapping IP address with your VPC
- You want to share your VPC with external customers but do not want traffic to leave the AWS network
Note that VPC endpoints are virtual devices that are highly available, redundant, and horizontally scaled.
Today’s article will focus on the two types of VPC endpoints:
- Gateway endpoints
- Interface endpoints
What is VPC interface endpoint
An interface endpoint is an elastic network interface (ENI) similar to a virtual network card but with a private IP address. The private IP will be from the IP address range of the subnet already specified by the user. This ENI will act as the main entry point for the traffic going to any supported AWS service.
Using an interface endpoint, you can connect your private IP address to different AWS services like an elastic load balancer, cloudformation, SNS, S3, etc. Interface endpoints also allow you to connect to supported marketplace partner services which are hosted by AWS partners or customers in their own VPCs. Your security group manages the traffic from the VPC resources to the endpoint ENI. PrivateLink then ensures that the VPC traffic to other AWS services does not go to the public internet.
The VPC interface endpoint is not free. You will be charged based on the usage and data processing rates for privatelink. Charges for creating and using interface endpoints are on top of that.
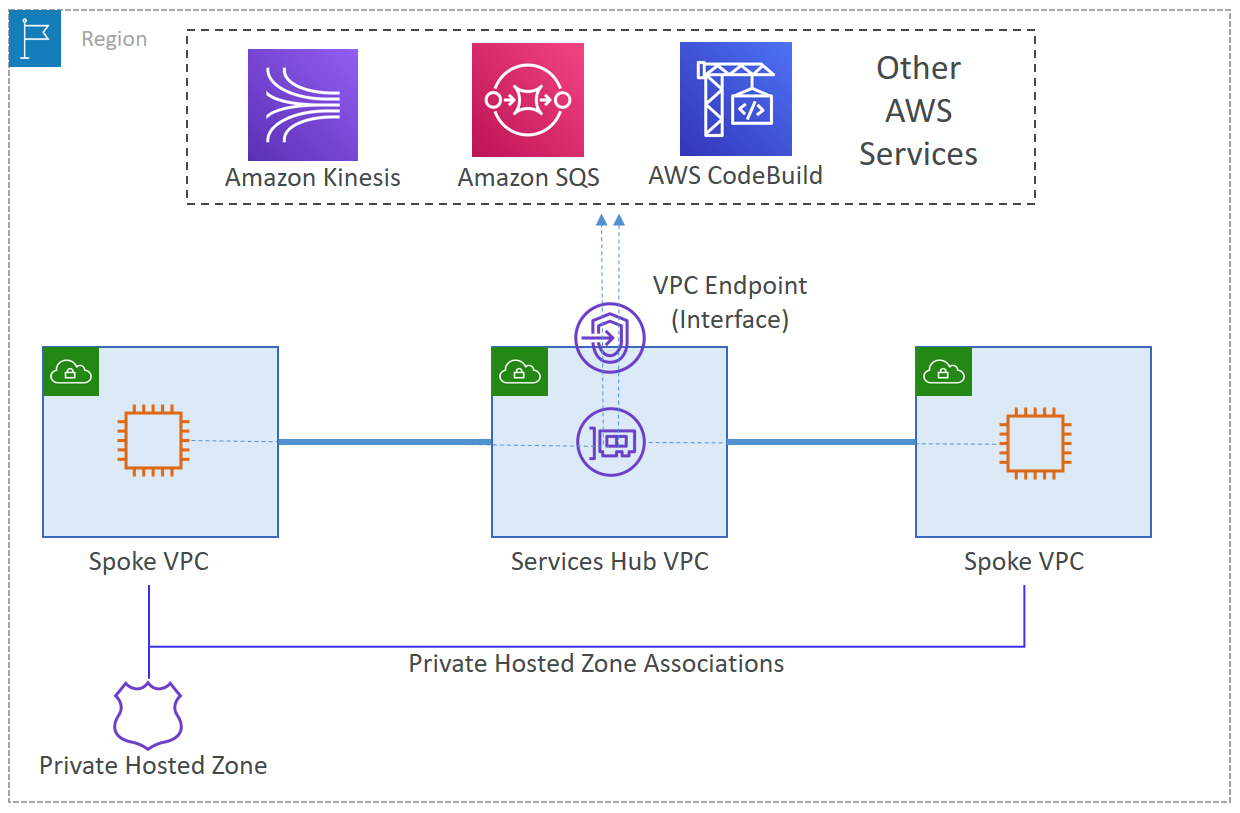
If you look at the diagram above, you can see that the endpoint ENI acts as a central point for traffic to supported AWS services, and this communication is through the private IP address, so the traffic does not leave the Amazon network.
How VPC interface endpoint works
- Create a new interface endpoint. Provide the name of the AWS service or endpoint service with which you want private connectivity.
- Create a network interface ENI and select the subnet to use the interface endpoint.
- From the IP address range of the subnet, a private IP is assigned to the endpoint network interface. This private IP address will be retained until the interface endpoint is removed.
- The private IP address ensures that the traffic does not leave the Amazon network without making any changes to the route table.
Note that after May 2022, the VPC interface endpoints also support IP V6 apart from IP V4.
What is VPC gateway endpoint
Consider a scenario where you have to access S3 from your EC2 instance in a public subnet. As the subnet has an internet gateway attached, the traffic to S3 will go through the public internet. However, the problem arises if your instance is in a private subnet and does not have any NAT gateway/instance attached or you cannot afford charges of NAT gateway. Currently, AWS S3 and DynamoDB are the only services supported by gateway endpoints. Using Gateway endpoints does not incur any data processing or hourly charges.
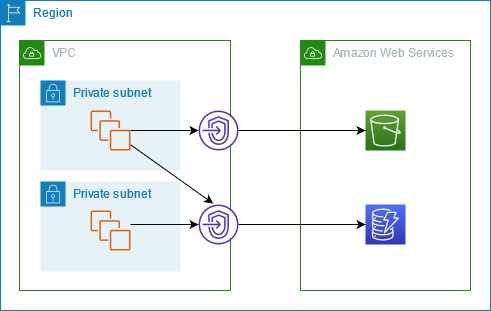
The above diagram shows that EC2 instances in the private subnet are accessing S3 and DynamoDB through gateway endpoints. One gateway endpoint is for S3, while another one is for DynamoDB. This traffic does not leave the amazon network, and it does not enter the public internet. As a result, communication is not only secure but fast as well. As it is free, you should take advantage of gateway endpoints whenever you can.
How VPC gateway endpoint works
- You create a VPC gateway endpoint.
- You select the VPC route tables for the subnets you enable.
- AWS automatically adds new routes to each route table that you select. The target is the gateway endpoint; the destination will be a prefix list for the associated AWS service.
- There is no need to explicitly make the instances to use the gateway endpoint to access the gateway services. All instances in the subnets associated with these route tables will automatically use the gateway endpoint.
The entry in the route table cannot be deleted unless the associated endpoint is deleted. In the example above, two endpoints were created in the same VPC, one for S3, and one for DynamoDB. The gateway endpoint is only available in the region it is created, so you need to create it in the same region as your VPC resources.
To date, gateway endpoints only support IP V4 and do not support IP V6.
Key differences between Interface endpoint and gateway endpoint
Below you’ll find the differences between the VPC interface endpoint and the VPC gateway endpoint.

Use Cases
Below are some of the use cases for VPC endpoints.
Use Case 1: Replacing NAT Gateway with Interface endpoints
A cloud-native application uses Databricks and ECS intensively. A large volume of data is transferred between ECS and Databricks frequently. Currently, the company is using NAT gateway for the following:
- Fetching TB’s of container images data from AWS ECR where container images are stored.
- Fetching TB’s of business data traveling between ECS and databricks
Thousands of dollars are spent because of data transfer charges of NAT gateway. You can create AWS VPC interface endpoints and then register them with Databricks. Each Databricks control plane publishes two VPC endpoint services for PrivateLink so that the communication does not leave the Amazon network. Routing traffic this way will save a lot of data transfer costs. Even if you add fault tolerance by adding one VPC endpoint per availability zone, it will still be much more economical compared to the cost incurred on the NAT gateway.
Use Case 2: Adding gateway endpoints for S3 intensive workload
Imagine a web crawler application that contains different web crawlers. The sole job of web crawlers is to crawl different websites, extract the data, and store the data in S3 buckets. In the traditional approach, NAT gateway is used to give internet access to these instances where the application is deployed because instances are placed in a private subnet. As a result, the data transfer charges to S3 are huge.
Now we can use the gateway endpoint to S3 to save data transfer charges of the NAT gateway. However, we still need internet access so that crawlers can access the websites, so we will add a NAT gateway as well. Note that we can have both the NAT gateway and gateway endpoint in the same subnet without any problem. The traffic to S3 will use the gateway endpoint – hence no charges. The traffic to other websites will use the NAT gateway. We can also use interface endpoints for AWS services other than S3 and DynamoDB.
Use Case 3: Private Access to SaaS based applications
Let’s say you have a SaaS-based application deployed in a private subnet in an AWS VPC. You want other AWS customers to access the services exposed by your SaaS application privately exposing your SaaS application services to the public internet. Here is how we can use VPC endpoints in this case:
- You will add a Network Load Balancer to relevant EC2 instances in your Amazon VPC, which will represent their endpoint service.
- AWS customers having their applications in their own VPC will be given access to the endpoint service and will create an interface endpoint in their respective VPC that is linked with the endpoint service.
- This will allow other AWS customers to privately access your SaaS application services from within their own VPC.
- Even the customers who do not have any of their applications hosted on AWS and want to consume your SaaS application services privately can utilize AWS Direct Connect for private connectivity to your SaaS application services.
In conclusion, the following are typical use cases for the gateway endpoint and interface endpoint:
- Use a gateway endpoint if you want to connect to S3 or DynamoDB privately
- Use the interface endpoint for everything else
Learn how to Master the AWS Cloud
AWS Training – Our popular AWS training will maximize your chances of passing your AWS certification the first time.
Membership – For unlimited access to our entire cloud training catalog, enroll in our monthly or annual membership program.
Challenge Labs – Build hands-on cloud skills in a secure sandbox environment. Learn, build, test and fail forward without risking unexpected cloud bills.





Responses