Secrets, cryptojacking, and AWS
Please use the menu below to navigate the article sections:
The Problem

Security researchers stumbled upon a long-lasting cryptojacking saga called “EleKtra-Leak.” In this cyber odyssey, mischievous culprits clone public GitHub repositories, making off with exposed AWS credentials. Specifically, key pairs are used to access the victim’s AWS accounts. The “clone and exploit” happens within minutes of an unaware victim accidentally posting a key pair. They then unleash a legion of Amazon Elastic Compute Cloud (EC2) instances to mine the cryptocurrency Monero. Researchers witnessed a staggering 474 miners controlled by what they charmingly call “potentially actor-controlled EC2 instances.”
AWS tries to help with its security practices, diligently alerting when credentials have been compromised. If AWS determines a key pair has been compromised (in this case, made public), they try to shut down the crypto criminals by applying the AWSCompromisedKeyQuarantine policy to the customer’s key pair. (Note: If you get an email from AWS about this policy being applied to your account, READ IT…they are trying to help.). However, our hackers are very good at unearthing AWS keys that the AWSCompromisedKeyQuarantine policy misses. Later in this article, we will give you a best practice to stop this from happening to you.
Cyber researchers have confirmed that the attackers indeed grab credentials from GitHub, despite AWS policies playing a rapid game of catch-up. Our actors are crafty, using methods beyond the researchers’ detective skills. The experts predict that credentials might also be sourced elsewhere, adding a dash of mystery to the plot.
Once they get their grubby hands on AWS credentials, our cyber rogues, working from behind the curtain of a VPN, go into recon mode. They snoop around the account, checking out the regions like spies scoping out their turf. Then, they get to work, creating security groups and launching EC2 instances across every enabled region. In a synchronized dance across multiple regions, they perform more than 400 API calls in a mere seven minutes, leaving behind a CloudTrail of breadcrumbs. All this is done by hiding as much as possible behind the secrecy granted by only using VPN connections to AWS.
Now, here’s where it gets interesting. The EC2 instances they summon are not small; think more like the c5a.24xlarge with 96 vCPUs and 192 MiB of memory! Why such blatant power grabs? Because when you’re cryptojacking, you need the VIP treatment – the processing power to mine Monero at warp speed. Then, in a brilliant twist, Google Drive hosts their mischievous mining payload. This is a rather clever move, as Google Drive’s URLs are like anonymous tips, leading investigators on a wild goose chase. These digital rogues remain elusive, dabbling in crypto with Monero’s privacy cloak, making them harder to catch.
Note: In case you are wondering, the on-demand cost of a c5a.24xlarge, as of November 2023, is $3.696/hour. With ten virtual machines mining for seven days, you would owe AWS just over $6,200!!!
Cybersecurity researchers recommend configuring secret scanning to prevent AWS credentials from doing the digital walk of shame on GitHub. And if any credentials do the unexpected and show up, cut the API connections immediately. It’s the cybersecurity equivalent of a superhero swooping in to save the day. And that, dear readers, is the tale of EleKtra-Leak – a cyber romp filled with intrigue, mischief, and a dash of Monero mining madness.
The Solution
“Fine, fine, fine! How do I help stop this from happening to my EC2 garden!” Well, it’s pretty easy. Check it out:
Log into your personal or organizational GitHub account and click on your avatar icon in the top right corner (in fact, you should check all GitHub accounts you might use, sending friendly messages to the admin of accounts where you have no control) and then click on Settings.
Once the Settings page opens, under Security, select Code security and analysis in the left menu.
In Code security and analysis, scroll to the bottom of the Secret scanning section. You have two options to enable:
- Secret scanning: This will start scanning any new repos you create.
- Push protection: With push protection, if anyone sends an update (a “commit” in git terminology) that contains a supported secret, the commit is blocked.
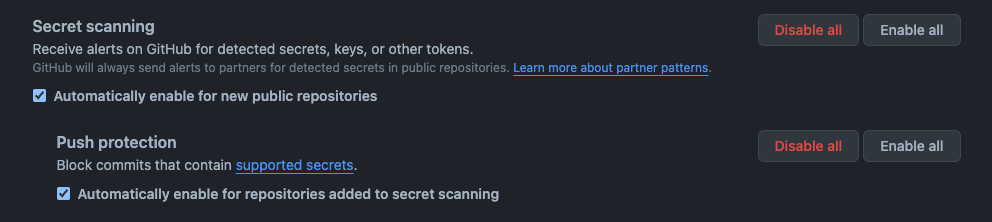
The Recommendation
Enable both options! For both options, select the Enable all button, and that’s all you have to do to improve your security.
Click the image above to watch this video from our youtube channel
The Special Note
Now, a special note is required. Notice that the language in the GitHub secret scanning option says, “Automatically enable for new public repositories.” That is to say, if you already have a compromised key in a repo, GitHub will not catch it.
The Closing
Remember, in the ever-evolving landscape of cybersecurity, complacency is the enemy. Embrace a proactive approach, fortifying your digital fortress with the unwavering support of automated systems like AI and automatic scanning. So, stay engaged with the latest news, keep your training ongoing and relevant, and make enabling security features the default behavior for yourself and your organization.
…and help keep that AWS bill down.
Ready to Take Your Tech Career to the Next Level?
At Digital Cloud Training, we’re dedicated to your success. Our courses offer up-to-date content, equipping you with the expertise to stand out in the competitive tech job market.
Our On-Demand Training allows you to learn at your own pace, fitting seamlessly into your schedule. Dive into the world of cloud computing whenever and wherever suits you best.
Our Challenge Labs provide practical, real-world scenarios where you can apply your newfound knowledge without the risk of unexpected cloud costs. Gain hands-on experience and sharpen your skills.
For those seeking an immersive experience, our Cloud Mastery Bootcamp delivers live, job-ready training. Led by industry experts, this accelerated program can get you certified faster than you thought possible.
It’s time to propel your tech career forward. Join us at Digital Cloud Training and unlock your full potential in the world of cloud computing.





Responses