AWS Transit Gateway | Overview and Best Practices
Please use the menu below to navigate the article sections:

This in-depth article on AWS Transit Gateway and its best practices provides a comprehensive explanation of the Transit Gateway concept and its significance in administering network infrastructure. You will gain a deeper understanding of how Transit Gateway can help you manage your network infrastructure more efficiently. The article includes hands-on instructions for its setup and testing Transit Gateway. We will show you how two different VPC’s can communicate with each other through transit gateway.
I. What is AWS Transit Gateway?
AWS Transit Gateway is a networking service that connects thousands of Amazon VPCs and on-premises networks using a single gateway. It uses a hub-and-spoke model to route all traffic to and from each VPC or VPN, and provides one place to manage and monitor it all. AWS Transit Gateway enables efficient and flexible connectivity and routing within AWS and for hybrid cloud scenarios12.
In simpler terms, AWS Transit Gateway is like a central hub that connects your Amazon Virtual Private Clouds (VPCs) and on-premises networks. It simplifies your network and eliminates complicated peering relationships. It functions as a cloud router, establishing new connections only once.
How AWS Transit Gateway works
Consider AWS Transit Gateway as the main hub in a city’s transportation system. Just as you’d use a central station to easily travel across the city, Transit Gateway lets you connect all parts of your network, like VPCs or on-premises networks, in a similar manner.
Instead of making separate connections between each network, which can quickly get complex, you connect them all to the Transit Gateway. When data needs to move from one network to another, it goes through the Transit Gateway, making your network architecture easier to manage and monitor. So, it’s like the central station for your data traffic.
Differences between AWS Transit Gateway and traditional network architectures
Consider first conventional network architectures. These are comparable to a telephone exchange from the past. In order to construct a direct line between each pair of telephones that needed to communicate, you would have to physically connect wires. This rapidly becomes complex and challenging to manage if there are numerous telephones. Each phone requires a separate line to communicate with other phones.
Now, consider the AWS Transit Gateway. Imagine that you have replaced your outdated telephone exchange with a modern mobile phone network. Instead of requiring a separate line for each pair of phones, they all communicate to the same network (such as the network of your mobile carrier). They can all communicate through this central network, eliminating the need to manage a multitude of individual connections.
Therefore, the primary distinction lies in the simplicity of management and scalability. With conventional network architectures, managing multiple connections can rapidly become complex. AWS Transit Gateway, on the other hand, simplifies network architecture by enabling all of your networks to connect to a central gateway. It’s as if you had one large switch that manages all your connections, making it much simpler to scale and manage your network.
II. Benefits of Using AWS Transit Gateway
Let’s imagine you’re the IT manager for a growing tech company. You have various departments each needing their own Virtual Private Cloud (VPC): Development, Sales, HR, etc. As your company expands, you’re also considering adding more VPCs, maybe even across different geographical regions. Let’s explore the numerous benefits of AWS transit gateway taking this example as a reference.
Simplified network management
Without AWS Transit Gateway, you’d need to make individual connections between each VPC. That’s like managing a massive spider web of connections. But with Transit Gateway, you create one central hub that all VPCs connect to. It’s like turning that chaotic spider web into a neat bicycle wheel, with the Transit Gateway as the hub and the VPCs as the spokes.
Enhanced security
With all VPCs connected through Transit Gateway, you can easily monitor and control traffic in one place, instead of hopping around different connections. It’s like having a security guard at the entrance of a building, checking everyone coming in and out.
Cost optimization
Without Transit Gateway, if VPCs communicate a lot with each other, you could rack up substantial data transfer costs because AWS charges for data moving between VPCs. But with Transit Gateway, data traveling between VPCs in the same region usually stays within the gateway, which can lower costs. Think of it like employees using internal mail to send documents to each other instead of paying for postage each time.
Improved scalability
Remember, your company is growing. AWS Transit Gateway can easily handle thousands of connections, making it simple to add more VPCs as your company expands. It’s like building a large office building with an open floor plan. As your company grows, you can easily rearrange the space to fit more desks without needing to construct additional rooms.
III. Getting Started with AWS Transit Gateway
Creating a Transit Gateway
Go to Transit Gateway after logging into AWS console. Click on the “Create Transit Gateway” button.
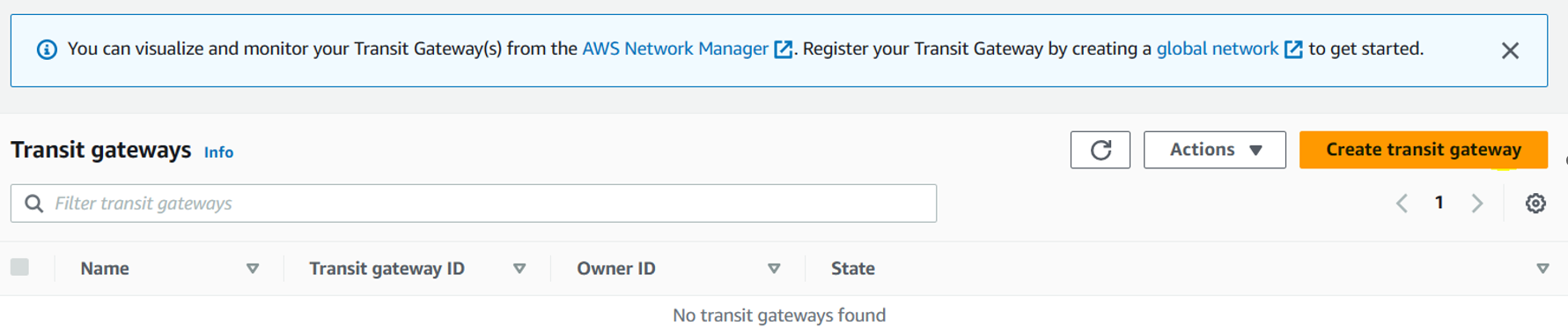
Then enter the name and description. You can leave the ASN field if you are not using BGP. For cloud based VPCs it is left empty.
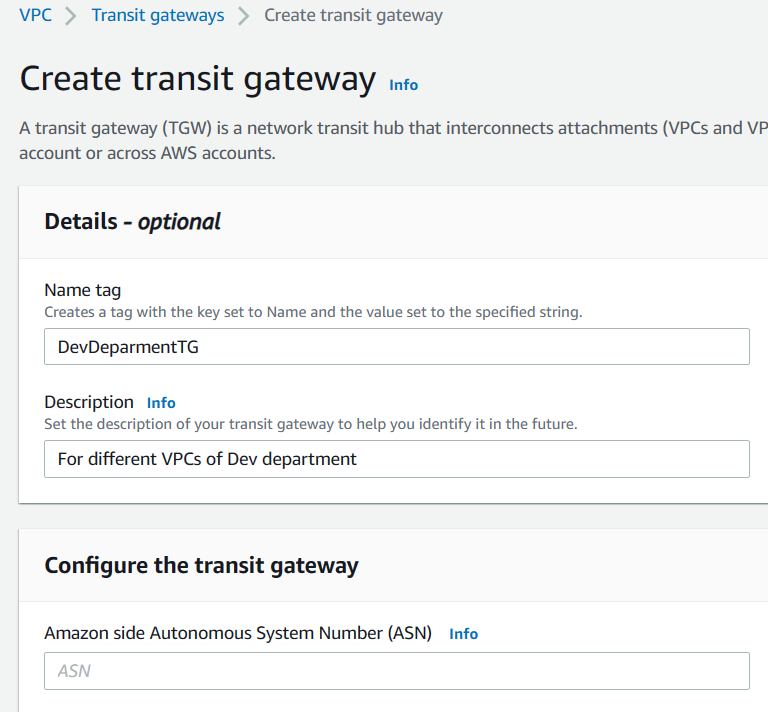
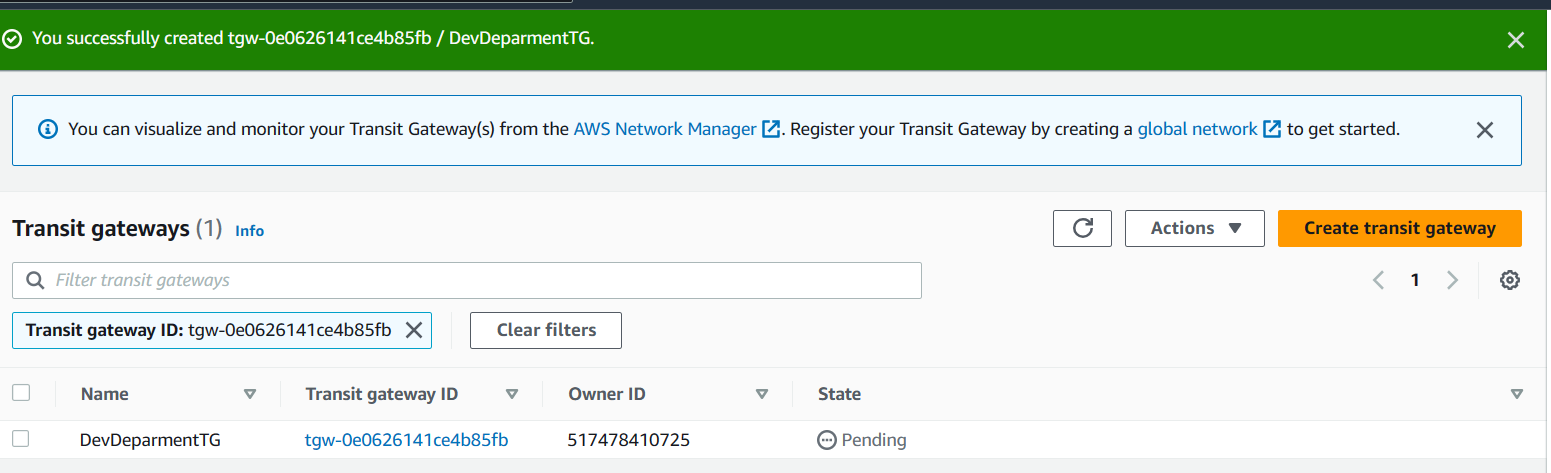
You can also add CIDR block but that is optional. Now you will see the gateway being created. As you can see in below screenshot, the state is pending but after a minute or two, it will be available.
Do not forget to add TG attachments as shown below.
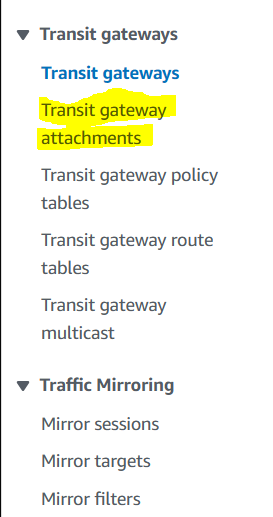
Now let’s create one TG attachment for each of the VPC’s.
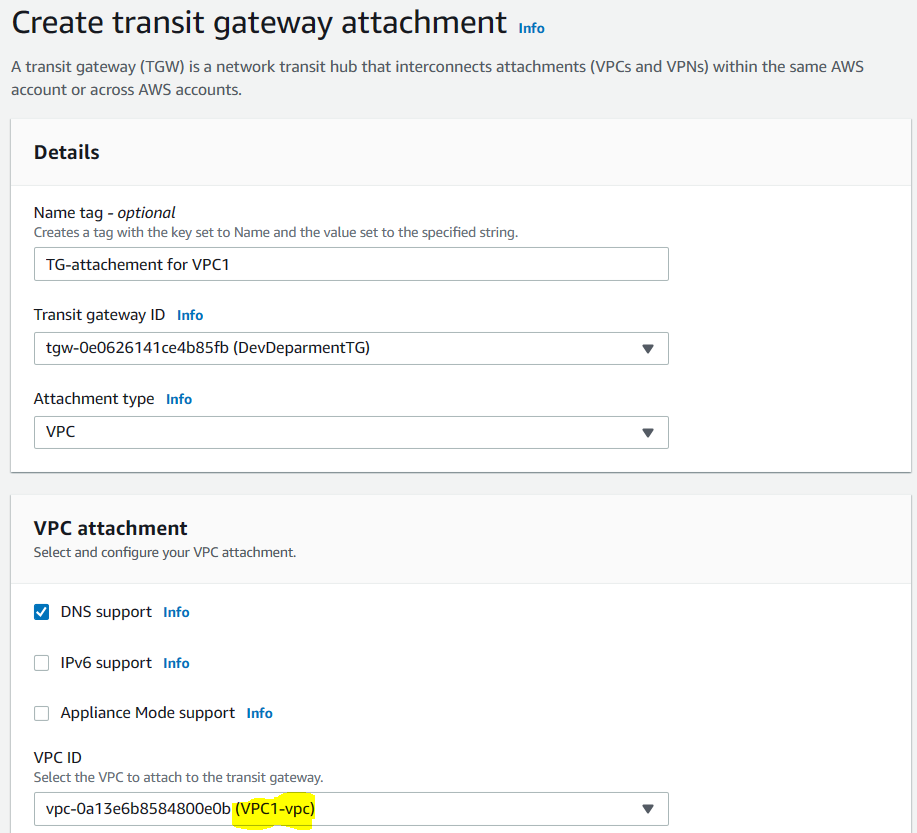
You can see this attachment was for VPC1. You can do the same for VPC2. Note that you will need to select the private subnet of the VPC when creating the attachment.
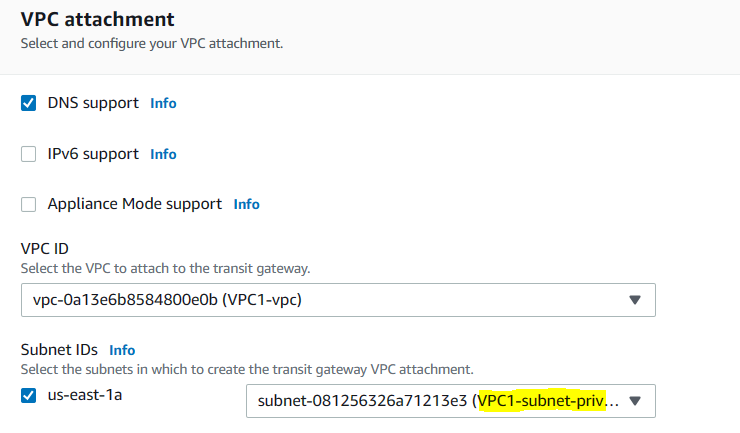
The next step is to configure your VPCs.
Configuring VPCs
Let’s create two VPC’s. Make sure that the CIDR block for both does not overlap. Go to VPC in your AWS console and click on Create VPC as below.
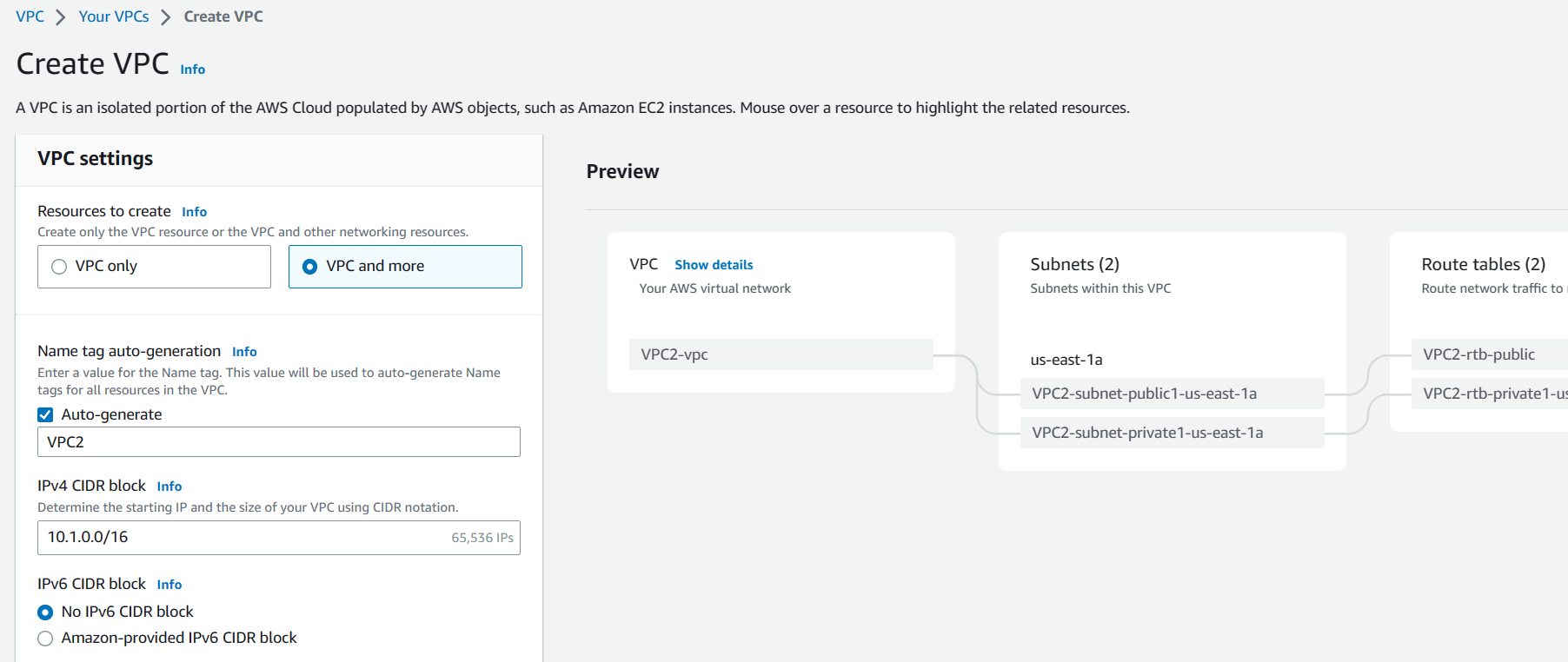
Now your VPC is being created.
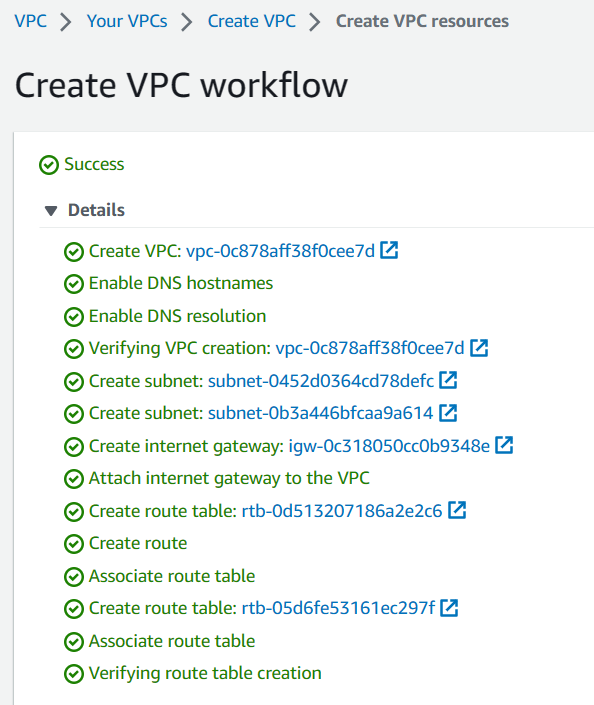
Creating routing tables
We need to create a route in each of the VPCs so that they know how to talk to transit gateway. Let’s add a simple route as below.
Go to private route table for VPC1 and add a route as shown below:
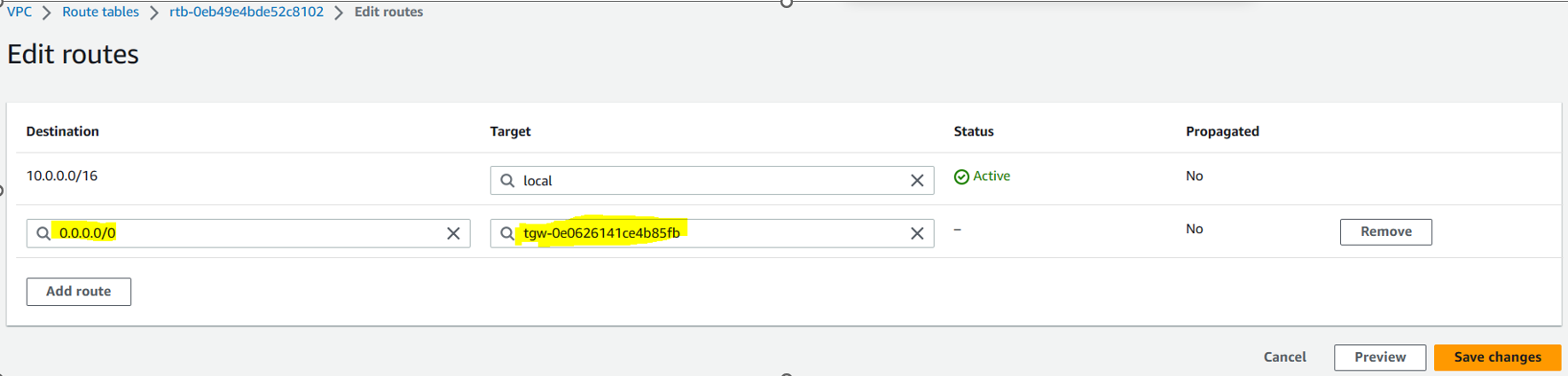
Then do the same for VPC2 private route table. When select target for VPC2 route table, select the TG attachment which was created for VPC2.
Now let’s create the security groups.
Configuring security groups
Note that you will need to create one security group for each VPC. See the example below.
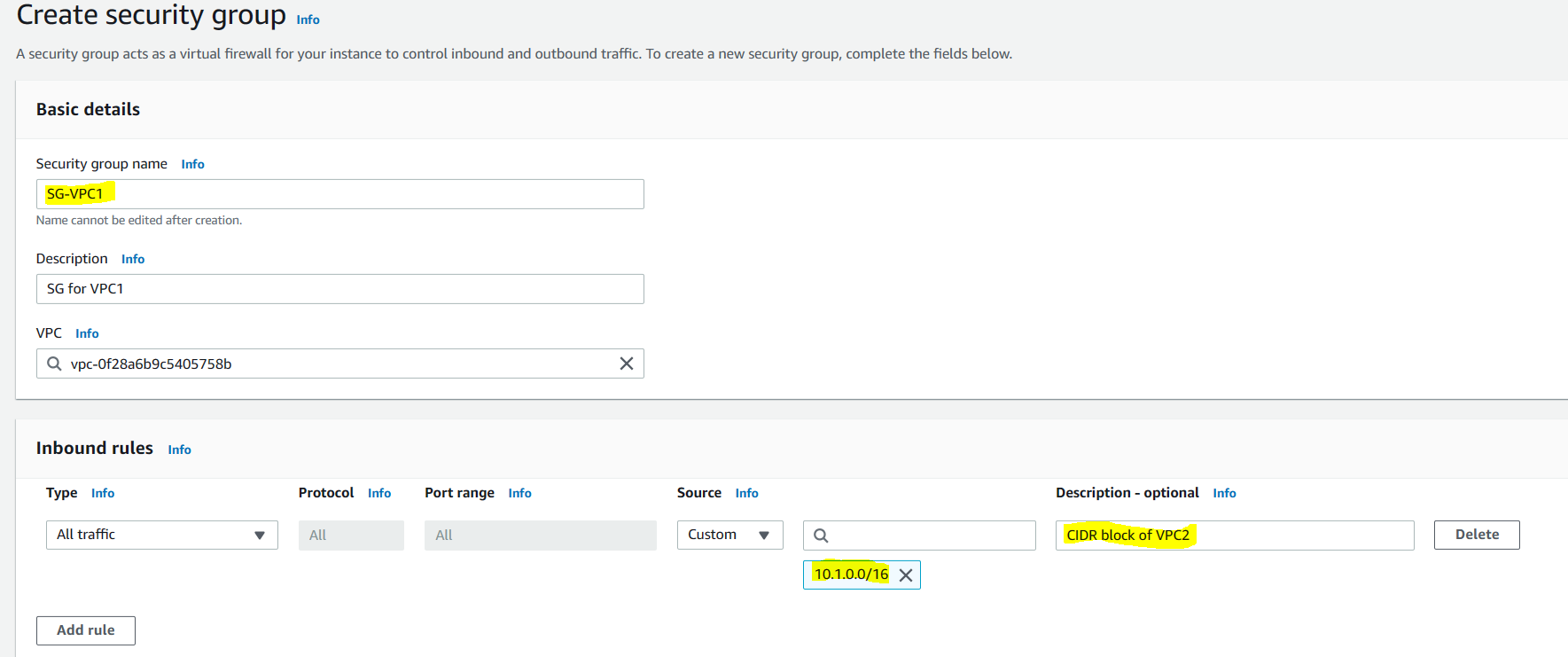
If you look at the source IP for the inbound rule of VPC1 security group, you will see that the CIDR of other VPC (VPC2) will be mentioned. Vice versa will be done for other VPC. No need to change outbound rule as SGs are stateful. After you have created security groups for both VPCs, lets create EC2 instances and attach these security groups.
Go to EC2 and create EC2 instance. The network details are most important here. If you take a look at the below screenshot, you will see that the EC2 instance is launched in a private subnet and that the security group selected is the same SG which we created for this VPC. Similarly, create another EC2 instance but in another VPC:
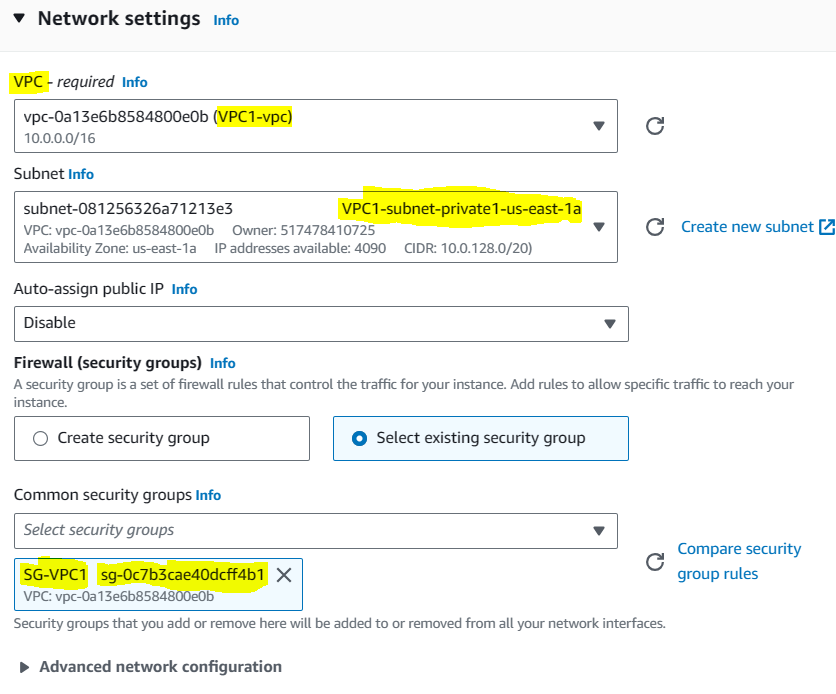
Now that both EC2 instances in their respective VPCs are created, they can talk to each other with their private IPs through transit gateway. Here is how we can test it:
- Create a bastion host EC2 in VPC 1 with a public IP address
- SSH into bastion host and then copy your keypair .pem file to any path in EC2 of VPC 1. Change the file permissions of this private file so that it is not editable by every one. E.g. chmod 400 /home/ec2-user/privatekey.pem
- In the SSH session of bastion host, issue below command to SSH into EC2 instance of VPC1, note that private IP of EC2 is used to connect with EC2 of VPC1:
ssh -i /home/ec2-user/privatekey.pem ec2-user@10.0.143.160
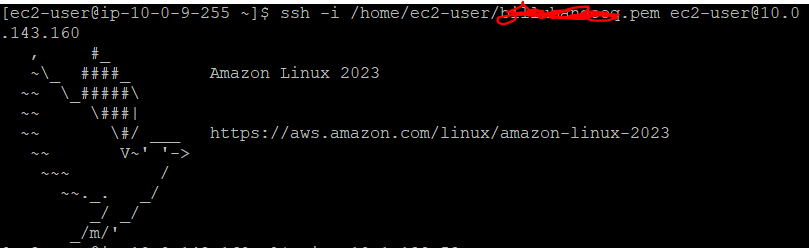
- Now that you have SSH into VPC1, let’s ping EC2 instance of VPC2 with its private IP
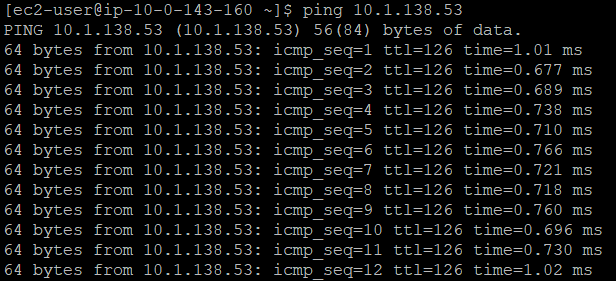
As you can see EC2 instance in VPC1 can successfully reach EC2 instance in VPC2 through the private IP. That is the magic of Transit Gateway.
IV. Use Cases for AWS Transit Gateway
Here are some of the important use cases for AWS transit gateway.
Enterprise-class network administration
Let’s use the example of a multinational corporation with numerous subsidiaries. Each division has multiple VPCs for various departments. The management of these VPC connections can become a nuisance. With AWS Transit Gateway, however, you have a central location to manage all these connections, thereby simplifying your life. All branches report to the central headquarter, similar to a large corporation.
Multi-account network management
Let’s consider the case of a company that has a multi-account AWS structure, which means that various departments or projects have their own AWS accounts to keep resources distinct. AWS Transit Gateway can manage connections between VPCs across multiple accounts, not just within a single account. It’s like a parent company (Transit Gateway) supervising and facilitating communication between subsidiary companies (AWS accounts).
Hybrid Cloud Networking
Another very useful scenario for transit gateway is hybrid cloud. If you are a business that utilizes both on-premise servers and cloud infrastructure and you seek a straightforward connection between these two distinct environments, then AWS Transit Gateway is the solution. It facilitates the connection of your on-premise network to your VPCs in AWS, creating a bridge between your on-premise resources and the cloud. Comparable to a manager who can communicate and coordinate tasks between two distinct teams within the organization.
V. Best Practices for Using AWS Transit Gateway
Tips for optimizing cost and performance
- Only utilize TGW (Transit Gateway) peering connections when required. Despite the fact that they facilitate connectivity between TGWs in various regions, they can increase costs. If you envision the TGW as a major airport, then peering connections are comparable to nonstop international flights; they are very convenient, but also quite expensive. Try to limit their usage whenever possible.
- Enable route table propagation as needed. It is similar to having an automatically updated address book; when you add a new contact (VPC), it is promptly added to your address book (route table). This reduces manual labor and aids in the prevention of human error.
How to improve security
- Effectively utilize Network ACLs and security groups. Consider these to be similar to bouncers at a nightclub; they only allow the desired individuals (traffic) to enter while keeping the undesirables (unwanted traffic) out. Your network is more secure if they are utilized effectively.
- By default, do not permit all traffic through your TGW. You would not give everyone the key to your house either. Only grant access when required.
Common errors to avoid
- Avoid making duplicate connections. It would be like constructing two bridges to traverse the same river, which would be costly and unnecessary.
- Avoid making your architecture overly complex. If you have a relatively straightforward network, you might not need multiple Transit Gateways or additional VPCs. Each new component you add is another item you need to manage, another potential point of failure, and another line item on your AWS bill.
- Remember to monitor and regulate. Since the cloud world is dynamic, regular inspections are required. Similar to a routine health checkup, you identify and treat prospective problems before they become major issues.
VI. Conclusion
Recap of the benefits of using AWS Transit Gateway
If your network is growing with increasing complexity, AWS Transit Gateway can save your business as it cleans up your network. All VPCs link to a single, central hub, making it much simpler to manage and track.
Transit Gateway also reduces data transfer fees by keeping internal communication within the gateway. Instead of posting memos, your employees could send them via internal mail. Scalability is another strength of AWS Transit Gateway. The gateway can handle more VPCs as your organization grows.
Final thoughts and recommendations
The AWS Transit Gateway is worth considering if your company is expanding or has a complex network structure. It improves scalability, management, security, and cost. It’s an all-in-one networking solution.
Best practices can help you avoid mistakes and optimize cost and performance when setting up and managing your AWS Transit Gateway. To keep your network healthy, keep it simple, use security features, and monitor regularly. Don’t build two bridges when one will do, and only give out network keys when necessary.
In summary, handle AWS Transit Gateway as you would managing a growing company – with careful planning, strategic resource allocation, and regular audits to keep everything working well.
VII. Ready to Take Your Cloud Career to the Next Level?
At Digital Cloud Training, we’re dedicated to your success. Our courses offer up-to-date content, equipping you with the expertise to stand out in the competitive tech job market.
Our On-Demand Training allows you to learn at your own pace and on your own schedule.
Our Hands-On Challenge Labs gives you the opportunity to apply what you’ve learned in a real-world setting without the risk of incurring surprise cloud bills.
Our live, immersive Cloud Mastery Bootcamp gives you job-ready skills and help get you certified faster than you thought possible.




Responses